Azure Secure Admin Workstation posts:
- Part 1 – VDI Environment
- Resource Group, Host pool, Workspace, Application Group, created an Entra Group with the ‘Desktop Virtualization User’ role and tie them all together.
- Part 2 – Firewalls and VNets
- Vnets, Subnets, IPs AzureFirewalls, Routes, FW rules etc.
- Part 3 – Session hosts and access
- Adding our SAW VM to the HostPool, connecting and authenticating
- Part 4 – Configuring Entra SSO
- Getting Entra SSO working!
- Public GitHub project:
Context
In the interest of enabling source control and potentially automation, the deployment is conducted using PowerShell commands. In this example I am using Azure CloudShell, for manual and exploratory activities it is handy as it is secure, includes all required modules, removes any authentication faff.
- If you want to create Microsoft Entra joined session hosts, we only support this using the Azure portal with the Azure Virtual Desktop service. (Add session hosts to a host pool | Microsoft Learn)
- You can create session hosts and register them to a host pool in a single end-to-end process with the Azure Virtual Desktop service using the Azure portal or an ARM template. You can find some example ARM templates in our GitHub repo
Reference Materials
- See Part 1 references
- Add session hosts to a host pool – Azure Virtual Desktop | Microsoft Learn
- Prerequisites | Microsoft Learn
Key Terms
- Session Host: An Azure VM to the Application Group that we created in Part 1, this is what authorised users connect to.
- Registration Key: When you add session hosts to a host pool, first you’ll need to generate a registration key. A registration key needs to be generated per host pool and it authorizes session hosts to join that host pool. It’s only valid for the duration you specify. (maximum of 30 days validity), see: Add session hosts to a host pool – Azure Virtual Desktop | Microsoft Learn
Deployment Procedure
When using Azure CLI or Azure PowerShell you’ll need to create the virtual machines outside of Azure Virtual Desktop, then add them as session hosts to a host pool separately.
- Add members to the saw_user_group
- NOTE: handled in zoak-solutions/AzureVirtualSAW (github.com)
- NOTE: handled in zoak-solutions/AzureVirtualSAW (github.com)
- Generate a registration key
- When you add session hosts to a host pool, first you’ll need to generate a registration key. A registration key needs to be generated per host pool and it authorizes session hosts to join that host pool. It’s only valid for the duration you specify. If an existing registration key has expired, you can also use these steps to generate a new key.
- Create and register session hosts with the Azure Virtual Desktop service
- Can only be conducted via the Azure portal
Add Entra joined Session Host
Following is direct from Add session hosts to a host pool – Azure Virtual Desktop | Microsoft Learn:
- Sign in to the Azure portal.
- In the search bar, enter Azure Virtual Desktop and select the matching service entry.
- Select Host pools, then select the name of the host pool you want to add session hosts to.
- On the host pool overview, select Session hosts, then select + Add.
- The Basics tab will be greyed out because you’re using the existing host pool. Select Next: Virtual Machines.
- On the Virtual machines tab, complete the following information:
- (this is for our use case and assumes you followed Part 1, of course customise this as appropriate)
- Name prefix: SAW
- Availability options: No infrastructure redundancy required
- Security Type: Trusted launch virtual machines
- Enable secure boot: True
- Enable vTPM: True
- Integrity monitoring: True
- Image: Latest Windows 11 Enterprise multi-session
- If we select Personal instead of Pooled in Part 1, we would have non-Enterprise options here…
- Virtual machine size, Number of VMs, OS disk type
- Use case dependent with no impact on procedure/security
- Boot diagnostics: Enabled with managed storage account
- Network and security
- Virtual Network: SAWVnet
- Subnet: SAWSubNet
- Network security group type: Basic
- Public inbound ports: No
- Domain to join
- Select which directory you would like to join: Microsoft Entra ID
- Enroll VM with Intune: Yes
- Virtual machine administrator account
- Required for Azure to provision the VM, once it joins Entra and Intune your Configuration Profile should remove the local administrator
- Custom configuration
- Custom configuration script url: None for now…
- Tags?
- Suggest adding ‘ResougeTag:AzureSAW’ for now… tags can be handy
- Download a template for automation, suggest doing this as a default behaviour
- Create!
Post Host Deployment
- After launching your first Session Host, Azure will take several (20?!) mins to deploy the session host and add it to the Host Pool. You can verify this was successful via Host pools – Microsoft Azure:
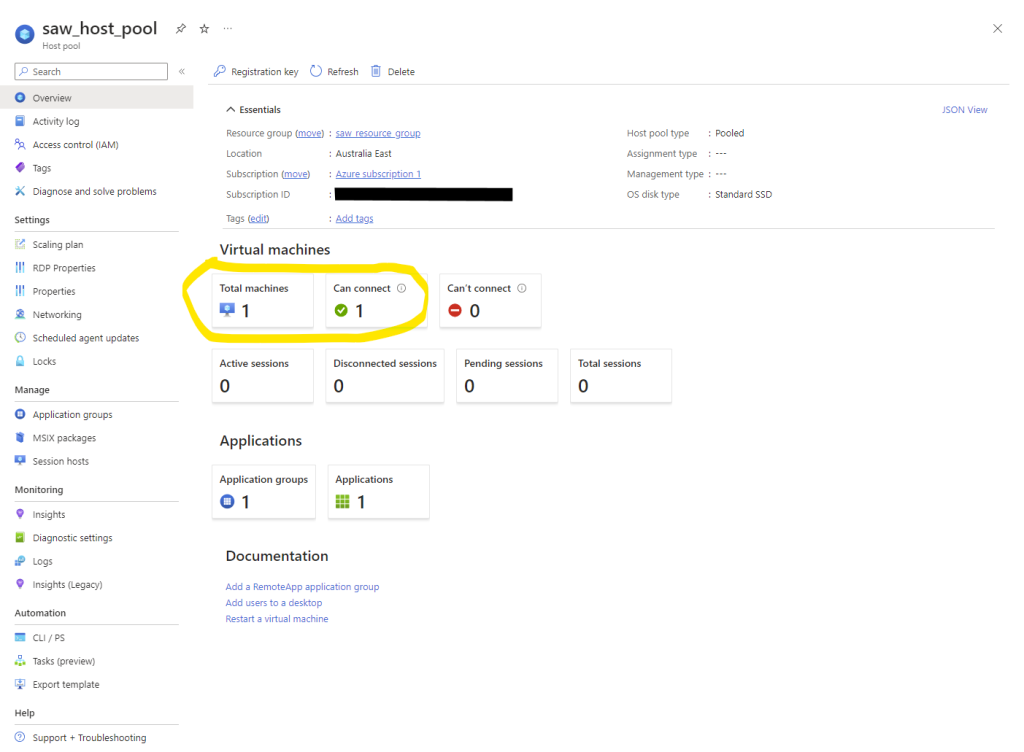
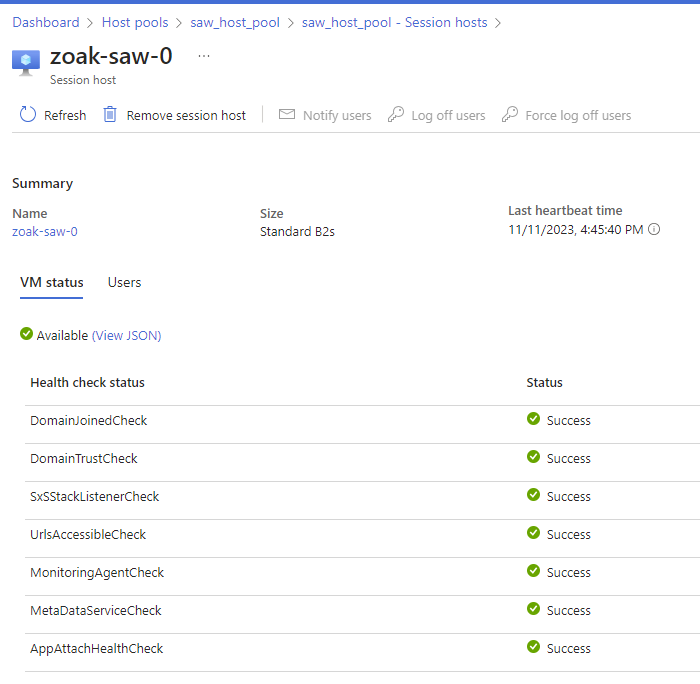
Enable Entra ID SSO
- Whilst this should be included in the scripts (at some point)… ensure the host pool -> RDP Properties (Noting: Configure single sign-on for Azure Virtual Desktop using Microsoft Entra authentication – Azure | Microsoft Learn)
- Didn’t work out of the box for me so made Part 4 – Configuring Entra SSO to track what needed to be done.
Troubleshooting
- Azure Virtual Desktop unable to access required network endpoints for provisioning
- Fix in test case: Ensure Azure Firewall Policy has all required endpoints allowed
- If you are able to connnect to the SAW, but unable to authenticate, check
Disk Encryption???
- Does enrollement in Entra and Intune enable Intune managed Bitlocker? (removing need for Azure managed Bitlocker?)
- Enable Azure Disk Encryption for Windows VMs – Azure Virtual Machines | Microsoft Learn
- Server-side encryption of Azure managed disks – Azure Virtual Machines | Microsoft Learn
PowerShell
- Assumes using an appropriately authenticated user with sufficient privileges
- zoak-solutions/AzureVirtualSAW (github.com)
- Source file below: AzureVirtualSAW/scripts/CreateRegKey.ps1 · GitHub
- NOTE: This is just for generating a Registration key, as we want Microsoft Entra joined session hosts, we can only create them via the Azure Portal as per: Add session hosts to a host pool | Microsoft Learn
RAW_https://raw.githubusercontent.com/zoak-solutions/AzureVirtualSAW/master/scripts/CreateRegKey.ps1
- After creating the Registration Key we can completed the Session Host deployment as per Add Entra joined Session Host
- zoak-solutions/AzureVirtualSAW (github.com)
- Source file below: AzureVirtualSAW/scripts/AddMembersToGroup.ps1 · GitHub
RAW_https://raw.githubusercontent.com/zoak-solutions/AzureVirtualSAW/master/scripts/AddMembersToGroup.ps1
Connect to my Azure Virtual SAW!
- Assuming your session host deployed successfully and your user has been added the $SAWUserGroup you can now access the SAW. As we are using the Azure Virtual Desktop Service:
- Microsoft manages the infrastructure and brokering components, enterprise customers manage their own desktop host virtual machines (VMs), data, and clients.
- So.. to connect we can use any/all of:
- Azure Virtual Desktop Store app for Windows (preview) | Microsoft Learn
- Remote Desktop app for Windows | Microsoft Learn
- Remote Desktop Web client | Microsoft Learn
- Remote Desktop client for Windows | Microsoft Learn
- Remote Desktop client for macOS | Microsoft Learn
- Remote Desktop client for iOS and iPadOS | Microsoft Learn
- Android and Chrome OS | Microsoft Learn
- Thin clients | Microsoft Learn
Extras
Set up Azure Virtual Desktop Client
- Download and install the Client App (or deploy to users via Add Microsoft Store apps to Microsoft Intune | Microsoft Learn)
- MS Store link: Azure Virtual Desktop Preview – Microsoft Apps
- Run it, on first run, assuming you installed unconfigured from the MS store you will be asked to subscribe (do this with your SAW access user)
- …. Thats it… you will see Session Host to connected to if all worked!
- Noting that Entra SSO was not working for me so… Part 4 – Configuring Entra SSO
Validate Session Host can talk to required Azure endpoints
You can validate that your session host VMs can connect to these URLs by following the steps to run the Required URL Check tool.
2 replies on “Azure Virtual Secure Administration Workstation – Part 3 – Session hosts and access”
[…] Part 3 – Session hosts and access […]
[…] Part 3 – Session hosts and access […]